I was literally in the middle of figuring out my New Year’s Eve logistics—trying to decide between two parties and a quiet night in—when my phone buzzed. I ignored it. Then it buzzed again. My watch tapped my wrist. Fine.
I looked down, expecting a text from a friend asking about plans. Instead, it was a notification from a tech discord I lurk in. Apple just pushed an emergency update. On December 30th. Right before the finish line of 2025.
Look, I get it. Nobody wants to stare at a progress bar while the “verifying update” spinner mocks you for fifteen minutes. We all have things to do. But you need to put your phone down, plug it in, and run this update right now. I’m not being dramatic.
The “Zero-Day” Nightmare Before New Year’s
Here’s the deal. Apple doesn’t usually push software updates during the holidays unless something is actually on fire. The engineers want to be on break too. If they are pushing code to millions of devices while most of the world is on vacation, it means the house is burning down.
The update addresses a critical security flaw in WebKit. If you aren’t a developer, WebKit is the engine that powers Safari. But it’s not just Safari. On iOS, it’s basically every browser. Chrome on your iPhone? That’s WebKit. Firefox on iOS? WebKit. The in-app browser that opens when you click a link in Instagram? You guessed it.
If WebKit has a hole, your entire digital life has a draft.
The specific issue here—and I’ll spare you the heavy hexadecimal details—is that processing “maliciously crafted web content” can lead to arbitrary code execution. In plain English? You visit a website. That website has some bad code hidden in an image or a script. Your phone tries to load it, gets confused, and suddenly that bad code is running on your device with the same permissions as the browser.
And it gets worse.
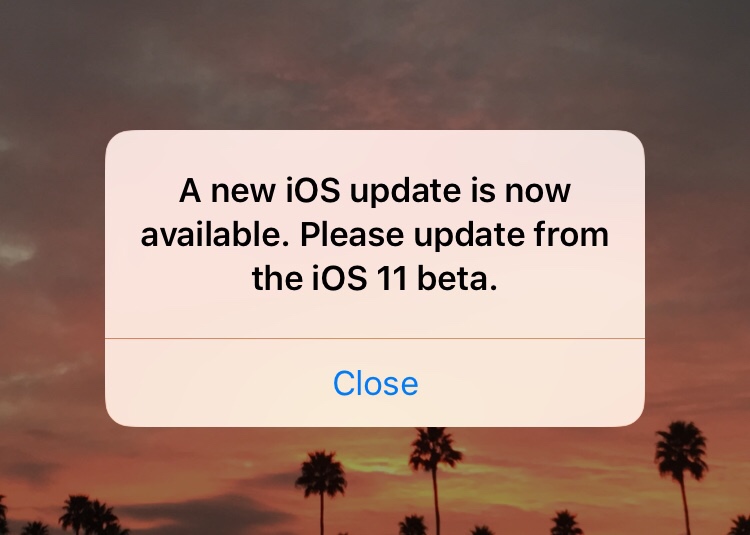
“Actively Exploited” is the Scary Part
Most security patches are preventative. Researchers find a bug, tell Apple, and Apple fixes it before the bad guys find it. We call those “responsibly disclosed” vulnerabilities. Boring, safe, good.
This isn’t that.
Apple’s release notes include the terrifying phrase: “Apple is aware of a report that this issue may have been actively exploited.”
Translation: Hackers found this first. They are using it right now. Real people are getting hit by this. It’s not a theoretical paper written by a grad student; it’s a weapon in the wild.
I see this happen all the time. People assume “hacked” means someone guessing your iCloud password because it was “password123”. But modern hacks are silent. You visit a URL, the page loads a split second slower than usual, and that’s it. You’re compromised. Spyware installed. Data siphoned.
That’s why this update—likely iOS 19.2.1 if you’re keeping track of the version numbers—is mandatory in my book. You don’t want to start 2026 dealing with identity theft because you were too lazy to reboot your phone.
My Uncle’s “If It Ain’t Broke” Logic
I was arguing about this with my uncle last night. He’s still running iOS 18 on his iPhone 15 because he thinks updates “slow down the phone” or “ruin the battery.”
“My phone works fine,” he told me. “Why mess with it?”
This logic drives me up the wall. It’s like saying, “My front door lock works fine, so I don’t need to lock it at night.” The functionality isn’t the issue; the security is. Yes, sometimes updates introduce bugs. I’ve written plenty of articles complaining about Apple breaking features or moving buttons around for no reason. I’m the first to complain when they mess up the Control Center layout.
But security patches are different. You don’t get to opt out of these unless you want to play Russian Roulette with your bank apps.
I grabbed his phone, forced the update, and waited the ten minutes. He grumbled. I didn’t care. Friends don’t let friends run unpatched WebKit vulnerabilities.
How to Fix It (Fast)
If you haven’t seen the prompt yet, don’t wait for it. Force it.
- Open Settings.
- Tap General.
- Tap Software Update.
- Refresh it by pulling down if you don’t see anything.
You’re looking for the latest patch. Depending on your device and region, it might just say “Security Response” or it might be a full point release. Just hit Update Now.
Pro tip: If you’re at a party tonight and the Wi-Fi sucks, don’t try to do this over a congested cellular connection. It’ll drain your battery and probably fail halfway through. Do it now, while you’re at home, or wait until you’re back on solid Wi-Fi tomorrow morning. Just don’t browse sketchy sites in the meantime.
Actually, scratch that. Do it now. Plug it into the wall, grab a coffee (or a pre-game drink), and let it do its thing. It takes maybe 10 minutes. You have 10 minutes.
One Last Thing
This vulnerability also affects iPads. So if you have an iPad Pro sitting on your coffee table that you use for Netflix, update that too. The same WebKit engine runs there. It’s easy to forget the tablet because we don’t carry it around in our pockets, but it has access to all your same emails, photos, and passwords.
I know, I know. It’s annoying. We all want technology to just be invisible and work. But until we invent unhackable code (don’t hold your breath), this is the tax we pay for having a supercomputer in our pocket. Pay the tax. Update the phone.
Happy New Year. Stay safe out there—digitally and physically.